As cyber threats continue to evolve, understanding the tactics used by attackers is crucial for bolstering defenses. This article delves into the latest SSH attack trends observed in 2024, using data gathered from a Cowrie honeypot. By analyzing login attempts, malware downloads, and attacker behaviors, we uncover the most common methods employed by cybercriminals and provide actionable insights for security professionals.
Introduction
SSH servers are a prime target for cybercriminals, and understanding their attack patterns is essential for defending against these threats.
Several years ago, I deployed a SSH and Telnet honeypot called Cowrie on an AWS instance. Over the years, I let it run in the background, occasionally taking a look at the logs and seeing how many hits it was getting. Eventually, I decided to start outputting the logs to a database and visualizing the data in Grafana. This allowed me to plot trending data, and see how attacks were evolving.
Cowrie is a medium to high interaction SSH and Telnet honeypot designed to log brute force attacks and the shell interaction performed by the attacker. In medium interaction mode (shell) it emulates a UNIX system in Python, in high interaction mode (proxy) it functions as an SSH and telnet proxy to observe attacker behavior to another system.
https://github.com/cowrie/cowrie?tab=readme-ov-file
Honeypots like Cowrie offer invaluable insights into real-world attacker behavior, enabling security professionals to stay ahead of emerging threats and refine their defense strategies. A properly constructed honeypot will allow an attacker to connect and run commands in an isolated environment, including downloading external malware. These files by default are not executed, but are saved for further analysis.
The Setup
Configuration Adjustments
To enhance the data collection capabilities of Cowrie, I made the following configuration adjustments:
- Configured the legitimate SSH service to listen on a non-standard port, allowing Cowrie to run on the default port 22.
- Enabled MySQL logging to allow easier parsing of historical data, which has proved useful in tracking trends.
Data Enrichment
Several Python scripts were built for data enrichment:
- Geolocation from IP address and add to database
- ASN from IP address and add to database
- Query malware lookup service by SHA256 hash
- Add malware type and signatures to database
Collected Data
As far as what’s being collected, the honeypot tracks incoming connections, successful authentications, malware downloads, and commands run once the attacker has connected. The honeypot is configured to accept most any password, which has both pros and cons.
Pros:
- We get to see more data revolving around post-exploitation activity, namely what is being run on the server, and what is being downloaded.
Cons
- Attackers manually attempting to brute force the server will easily be tipped off that it’s a honeypot if the first password attempt works.
With the honeypot up and running, the next step was to analyze the data it collected, leading to some interesting discoveries.
Key Findings
The analysis of the Cowrie honeypot data reveals a consistent and aggressive pattern of brute-force attacks, alongside noteworthy trends in malware downloads and attacker behavior. So let’s take a look at the identified SSH attack trends:
Brute Forcing
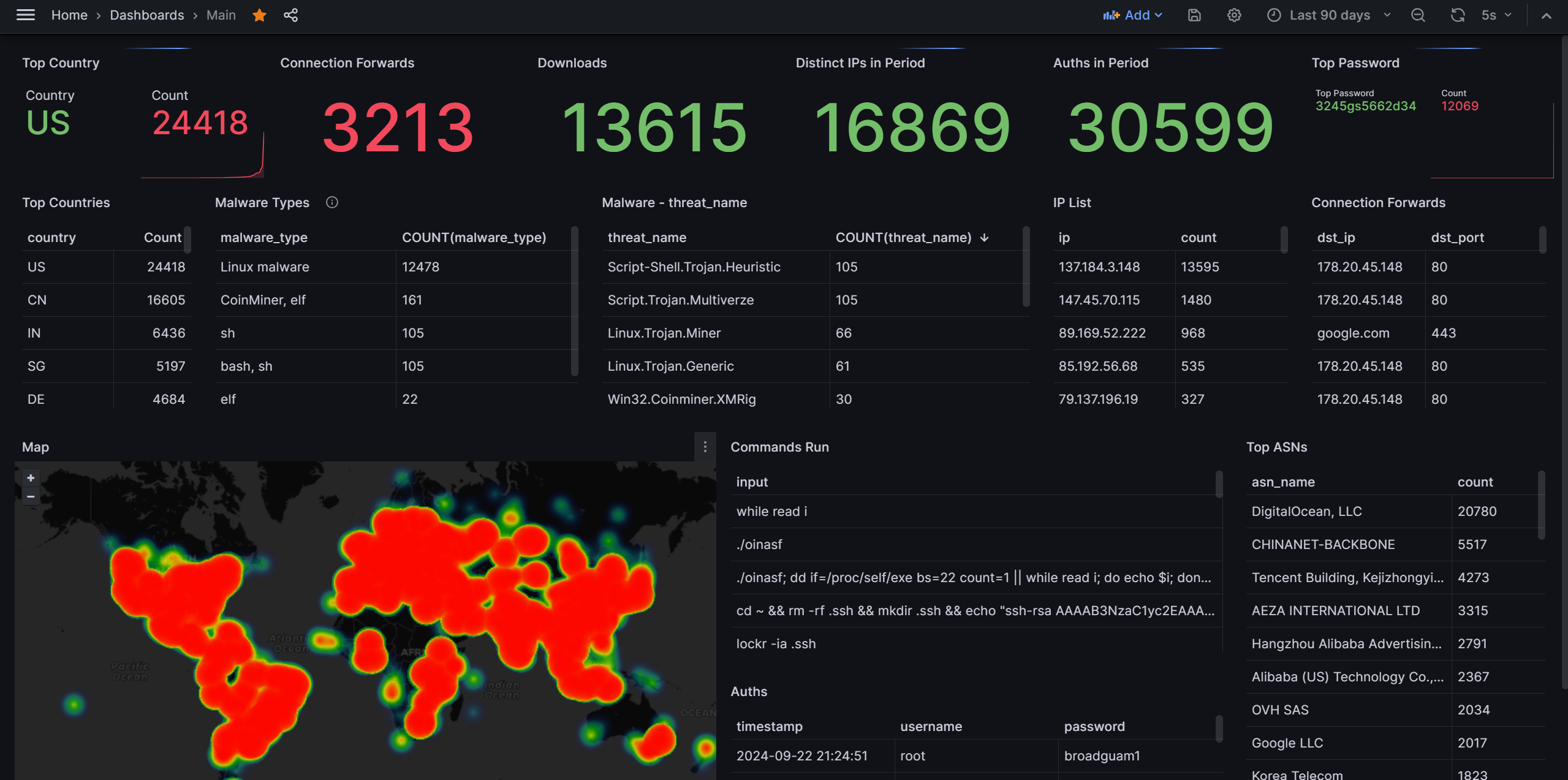
The number one take-away here is that password brute-forcing isn’t going away. Instead, it gets more and more common. In the last 24 hours, the honeypot has had 136 successful connections. When pushing this out to 90 days, we see a whopping 30,600 successful connections.
Over the past 90 days, the most common password was “3245gs5662d34” with 12,070 uses. As this honeypot is configured to accept any password, this means it was the first entry in the list being used. I have found several references to this password from other blog posts by other honeypot administrators, but so far have found no explanation for why this password is topping the lists.
As of this writing, the below is the 24-hour heatmap of attacks by location:
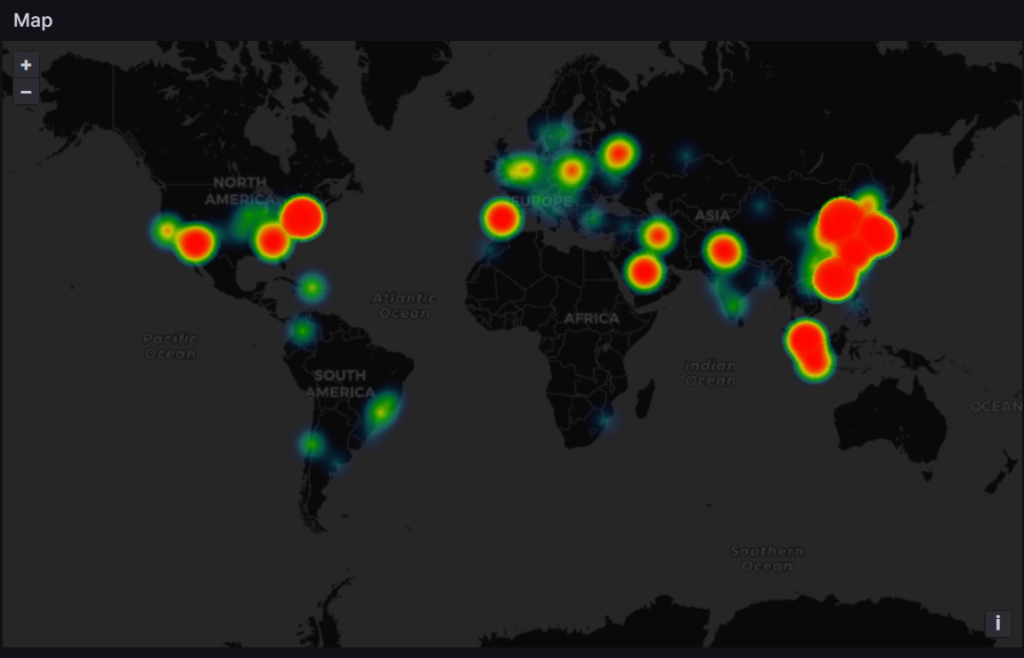
The primary sources for connections to the honeypot are spread between the United States, Europe, India, and China.
Over the past 90 days, the top ASNs were as follows:
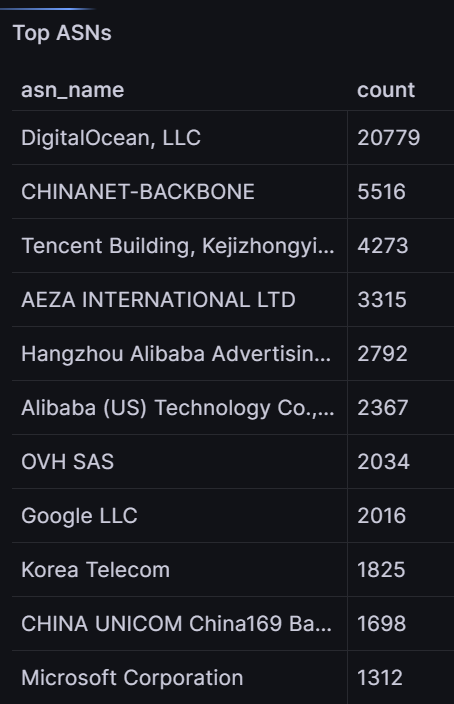
Tracking ASNs
High connection attempts from specific Autonomous Systems (ASNs) indicate that certain networks are either a hotspot for malicious activity or are being used as a base for launching attacks. This could imply a few scenarios:
- Malicious Infrastructure:
- These ASNs might be hosting compromised servers or malicious infrastructure, such as command-and-control servers, botnets, or staging points for attacks. Frequent connections from these ASNs suggest they are being used for large-scale, automated attacks.
- Poor Network Hygiene:
- A high number of attack attempts from a specific ASN might indicate that the network lacks proper security measures, making it an attractive target for attackers to hijack and use as a launchpad for further attacks.
- Geopolitical and Policy Factors:
- Certain regions or networks might have less stringent cybersecurity policies, making them more susceptible to being used for malicious activities. Understanding the geographic and administrative context of these ASNs can help in anticipating and mitigating threats.
- Targeted Campaigns:
- If an ASN is associated with a specific organization or industry, a high number of connection attempts might indicate a targeted attack campaign. This could be part of a larger strategy to compromise a specific sector or gain access to sensitive information.
Malware Download Trends
Within this same 90 day period, 13,616 files were downloaded.
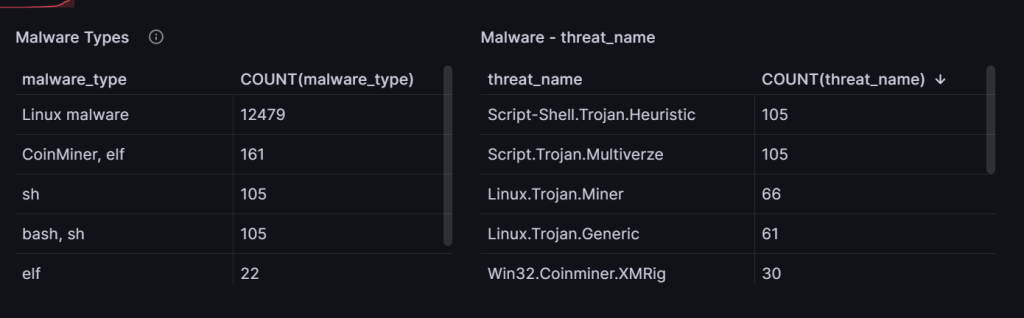
Identified Malware Types
- Linux malware (various instances of trojans designed for linux environments)
- CoinMiner, elf (A common tactic for attackers is to install cryptocurrency miners and generate crypto on stolen hardware)
- sh (malicious shell scripting)
- elf
Identified Malware Signatures
- Script-Shell.Trojan.Heuristic
- Script.Trojan.Multiverze
- Linux.Trojan.Miner
- Linux.Trojan.Generic
- Win32.Coinminer.XMRig
- Linux.Hacktool.Multiverze
- Win32.Trojan.Generic
- Linux.Trojan.Multiverze
- Linux.Exploit.Multiverze
Attack Patterns
The analysis of the Cowrie honeypot data reveals a consistent and aggressive pattern of brute-force attacks, alongside trends in malware downloads and attacker behavior.
Common Commands
The most common commands run on the honeypot after initial connection are:
- cd ~; chattr -ia .ssh; lockr -ia .ssh
- lockr -ia .ssh
- cd ~ && rm -rf .ssh && mkdir .ssh && echo “ssh-rsa
AAAA[truncated]oRw== mdrfckr”>>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~ - uname -a
- cat /proc/cpuinfo | grep name | wc -l
- rm -rf /tmp/secure.sh; rm -rf /tmp/auth.sh; pkill -9 secure.sh; pkill -9 auth.sh; echo > /etc/hosts.deny; pkill -9 sleep;
- cat /proc/cpuinfo | grep name | head -n 1 | awk ‘{print $4,$5,$6,$7,$8,$9;}’
- free -m | grep Mem | awk ‘{print $2 ,$3, $4, $5, $6, $7}’
- which ls
- ls -lh $(which ls)
This list of most common commands are primarily different ways to get information about the server. These commands allow the attackers to determine what kind of malware to eventually load on the machine, based on the architecture, OS, and CPU, and other metrics. The bolded and underlined entries will be addressed in the below “Interesting Cases” section.
Connection Forwards
Additionally, when looking at the most common connection forwards in the 90 day period, we see numerous forwards to google.com. However, we also see a large list of connections to “178.20.45.148,” which resolves to Russia, and is identified by IP Quality Score as “suspicious.”
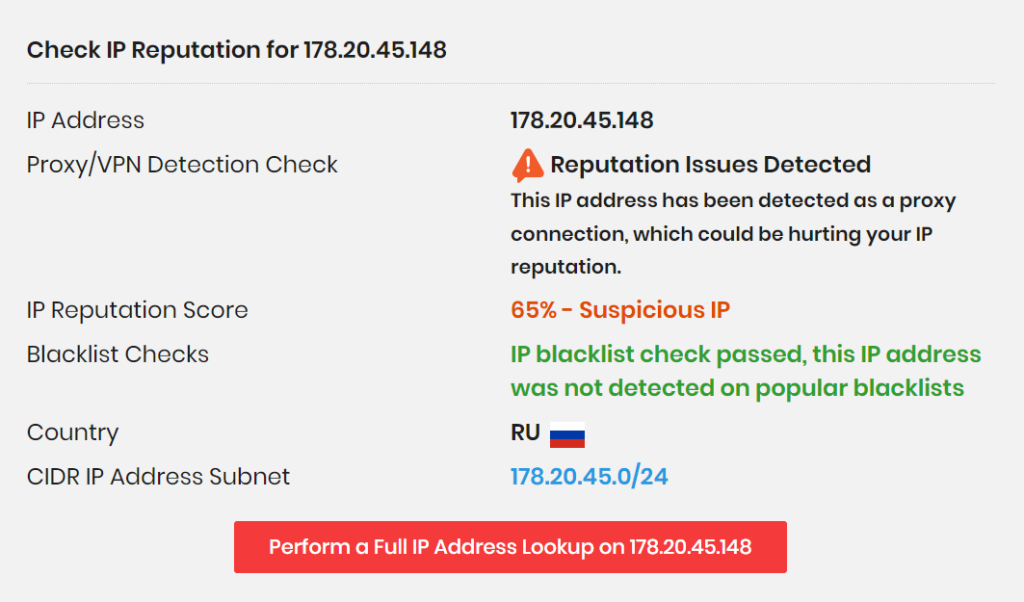
What does this mean? Connection forwards refer to the practice of forwarding network traffic from one host to another through an intermediate host. Attackers often use this technique to:
- Bypass Firewalls and Network Restrictions:
- By forwarding connections through the compromised host, attackers can access internal resources or networks that would otherwise be inaccessible due to firewall rules or network segmentation.
- Establish Persistent Access:
- Attackers can set up port forwarding to create backdoors that allow them to re-enter the compromised network even if their initial point of entry is detected and removed.
- Proxy Malicious Traffic:
- Compromised hosts can serve as proxies for routing malicious traffic, such as additional attacks or data exfiltration, making it difficult for defenders to trace the true source of the malicious activity.
- Hide Malicious Activity:
- By routing through multiple compromised systems, attackers can obfuscate the origin of their traffic, making it harder for network defenders to pinpoint the attacker’s true location and intent.
Interesting Cases
The Cryptominer
In the list in the last section, I’ve bolded a really interesting command though (as well as underlined some associated commands).
A particularly interesting command sequence observed was ‘cd ~ && rm -rf .ssh’. This command, executed 12,479 times over 90 days, highlights a common tactic used to gain persistent access and maintain control over compromised systems. Let’s take a closer look at why this command is so effective and how it is linked to cryptomining campaigns.
This blog post by Dan Goldin breaks down pretty well what’s happening here, but let’s take a quick look. First, the command is removing the .ssh directory, which is where authorized keys to connect to the server are stored. If the server is configured to only accept private key connections as opposed to passwords, this locks the user out of the server. The command then rebuilds the .ssh directory and adds the attacker’s public key to the authorized keys file. This means the attacker is now the only user able to log in via ssh to that user account. According to the blog linked above, this particular ssh key is associated with cryptominer malware, which checks out when compared to the earlier malware trends discussed.
Another blog, Port 22, provides further analysis on the MDRFCKR threat actor (named after the ssh key name). According to Port 22’s research, the other commands underlined above are also part of their attack chain.
Why Cryptomining?
Cryptomining malware is commonly observed in attacks for several reasons:
- Low Risk, High Reward:
- Cryptomining malware provides attackers with a relatively low-risk way to generate revenue using the resources of compromised systems. Unlike ransomware, which requires direct interaction with victims, cryptominers operate quietly in the background, often going unnoticed for extended periods.
- Automated Deployment:
- Many cryptomining attacks are automated, allowing attackers to spread the malware across numerous systems with minimal effort. Once deployed, the malware can continue generating cryptocurrency for the attackers without further intervention.
- Resource Utilization:
- Compromised systems, especially servers with powerful CPUs and GPUs, are ideal for mining cryptocurrencies. Attackers leverage these resources to maximize their mining output, making any system with substantial computational power an attractive target.
- Growing Popularity of Cryptocurrencies:
- The increasing value and ease of converting cryptocurrencies into real-world money make cryptomining an appealing strategy for attackers. As a result, cryptomining malware has become a popular choice for monetizing compromised systems.
Implications for Security
Okay, so that’s a lot of data. But what do these SSH attack trends mean for the average network administrator or security professional?
Malicious Activity
Brute-force attacks are just the beginning; once inside, attackers can use compromised SSH servers to escalate privileges, exfiltrate data, or launch lateral attacks. This underlines the importance of securing SSH servers with robust configurations and monitoring for anomalous activity.
Compromised servers are also used to proxy connections, which could be part of a wider attack chain, allowing a connection to bounce between multiple compromised systems before hitting their final target. This can cause costly reputation hits to businesses and organizations who unknowingly become part of the connection chain.
Attribution
For threat researchers, honeypot data like what we’re seeing in Cowrie can be useful in identifying new threat actor groups, like we discussed with MDRFCKR. Seeing how they operate, and what actions they take on compromised machines allow threat hunters and researchers to build new detections for endpoint detection, ensuring that organizations are able to easily identify these indicators of compromise.
Security Recommendations
So what can organizations do to protect their infrastructure?
- Implement IP and Geolocation Blocking:
- Block known malicious IP addresses and ASNs, especially those with high volumes of attack attempts. Geolocation blocking can also be used to restrict access from regions known for high malicious activity.
- Enable Multi-Factor Authentication (MFA):
- Enforce MFA for all SSH connections, making it significantly more difficult for attackers to gain access even if they have compromised passwords.
- Restrict SSH Access:
- Limit SSH access to only trusted IP addresses using firewalls or VPNs. Consider using non-standard ports and implementing port knocking or other techniques to obscure the SSH service.
- Harden SSH Configurations:
- Disable password-based authentication and only allow key-based authentication. Regularly rotate SSH keys and ensure they are stored securely.
- Deploy Intrusion Detection and Prevention Systems (IDPS):
- Use IDPS to detect and block suspicious activities, such as brute-force attempts or unusual connection patterns. An IDPS can provide real-time alerts and automated responses to potential threats.
- Monitor and Alert on Anomalous Activity:
- Implement logging and monitoring solutions to track login attempts, command executions, and connection forwards. Set up alerts for any unusual patterns or unauthorized activities.
- Segment and Isolate Critical Systems:
- Use network segmentation to isolate critical systems and services from general network access. Implement strict access controls to minimize the impact of compromised systems.
- Use Honeypots Strategically:
- Deploy additional honeypots with varying configurations to gather more diverse data and observe different attacker behaviors. Use the data to enhance security controls across your environment.
These measures, when combined, can help organizations defend against the observed attack patterns and reduce the risk of compromise.
Future Work and Monitoring
While this honeypot has been running for a few years, there are multiple changes that still need to be made to properly analyze the data and generate actionable SSH attack trends. Getting the data into a database and visualizing it in Grafana is simply the first step.
Future plans include correlating attack data with specific malware campaigns to identify emerging threat actor groups.
One of the biggest challenges in analyzing the downloads is the limitations of the VirusTotal API. VirusTotal has added some severe limitations to the free API, funneling users that want to build integrations towards their enterprise plans. For an independent researcher, these plans are simply unaffordable. For the moment, the scripts are using MalwareBazaar, though some hashes that are found on VirusTotal are not found on MalwareBazaar.
Conclusion
So to summarize, the Cowrie honeypot can monitor malicious attempts to attack SSH and Telnet servers, track post-exploitation activity, monitor malicious downloads, and identify new emerging threats. This enables security researchers to better track SSH attack trends over time.
For organizations looking to gain similar insights, deploying a honeypot can be a powerful tool. I encourage fellow security researchers to experiment with their own deployments and share their findings with the community.
Additionally, a honeypot deployed on an external facing network owned by an organization can allow their security team to monitor threats actually affecting them, and identify specific threat actors that may be tailored to their particular business or industry.