The term Internet of Things (IoT) has picked up in popularity as more and more devices are connected to the Internet. Everything from home refrigerators to industrial control systems have been found connected, and in many cases, with minimal to no security. What are the consequences? How should they be secured? Should IoT devices be avoided? Read below to find out.
Shodan
One way that these devices are found is through the search engine Shodan. Shodan was launched in 2009, and is used to find devices as opposed to websites. While typical search engines such as Google will search and index web content, Shodan searches and indexes service banners, which provides metadata from the server. Shodan searches and collects data on many typical ports, such as HTTP, FTP, SSH, and various mail protocols. Shodan also supports various filters, such as location, name, port type, etc., so the search can be highly fine-tuned.
A large number of different devices are indexed on the search engine, including power grids, gas stations, and nuclear power plants. This wouldn’t be as surprising, if most of these devices and systems didn’t run with default passwords, or in some cases, no passwords at all. We’ll look at that more in-depth below.
Current Issues
As stated above, many of these systems are connected to the internet with almost no security. Many of them that do have passwords are running defaults such as “password” or “1234.”
Notable examples of this are connected car washes. Security researchers have managed to turn on sprayers, shut bay doors, and move control arms, which could be used by a malicious attacker to cause significant vehicle or bodily injury. Along the same lines, several gas stations have been found with minimal security. In these cases, researchers were able to view and edit critical data, anything from the amount of fuel in the pumps, to turning specific pumps off and on.
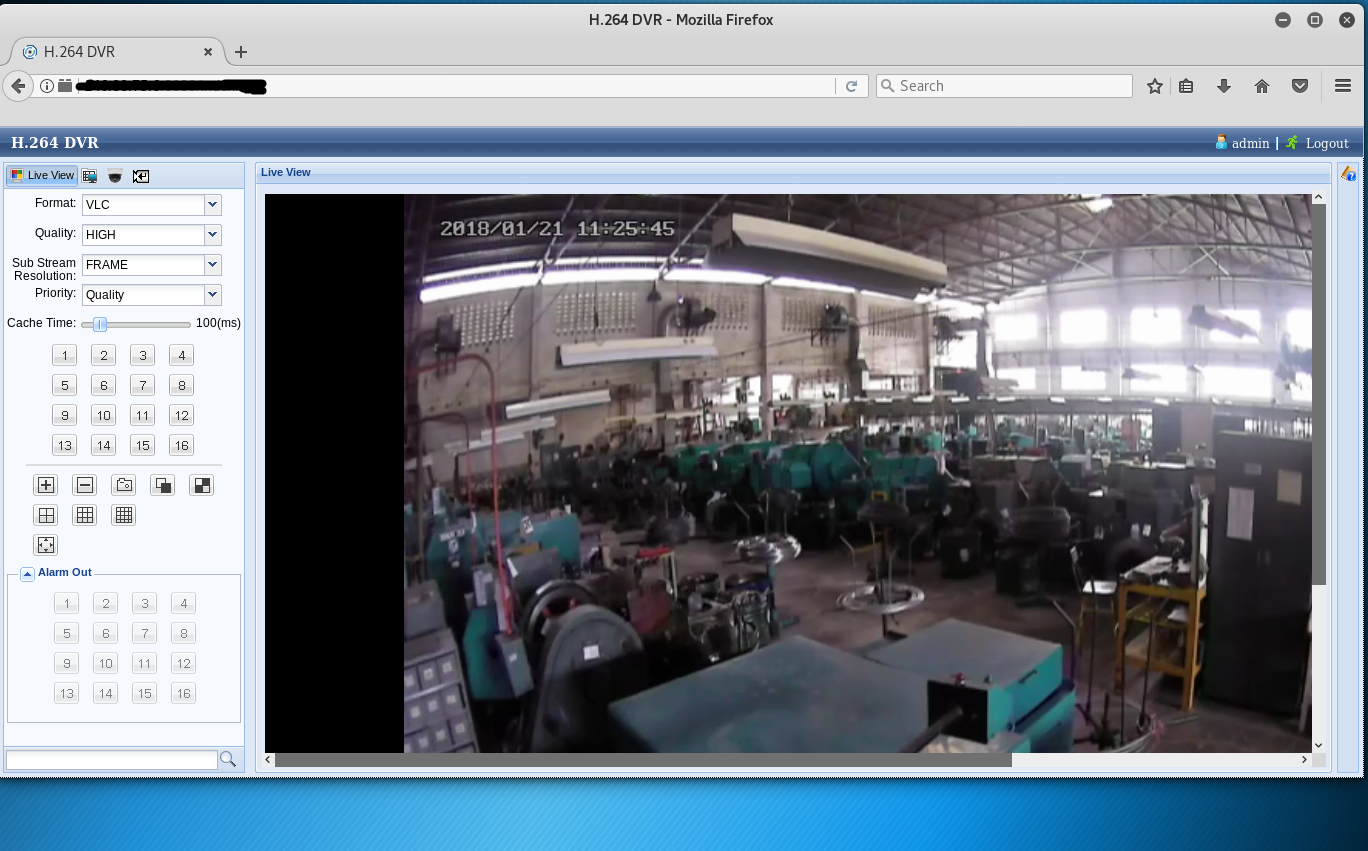
There are also examples of red light enforcement cameras connected to the Internet, accessible through multiple protocols. In many documented cases, these camera systems are accessible with no credentials required through a web browser or through Telnet. From here, critical settings can be changed, the system can be turned on and off, and the database of captured license plates can be downloaded. One researcher demonstrated putting the entire system in “test mode.”
One of the most common IoT devices found when searching Shodan is network cameras. Everything from home security cameras, warehouse security cameras, nanny cameras, baby monitors, and in some cases even desktop web cameras, are connected to the Internet. While many of these can have a purpose in being connected (being able to remotely view security footage, for example), a surprising amount of these are connected with the default settings never altered.
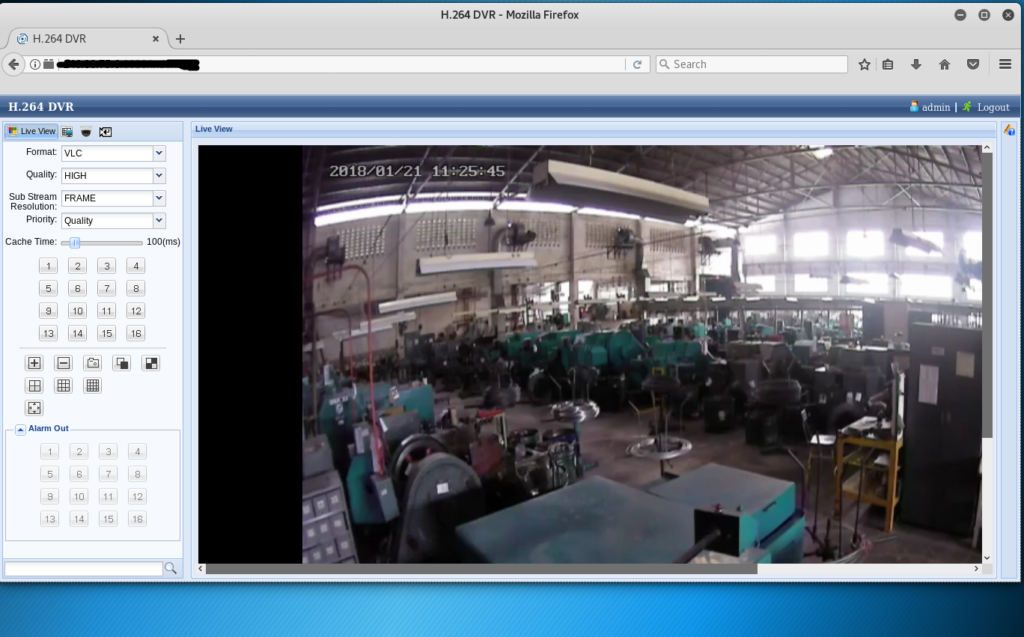
IoT devices are known to be a weak spot on networks. Attackers can use a poorly configured device to gain access onto a network, and from there gain access to other systems. This also applies to office networks, especially with Internet connected printers. Once the printer is compromised, the attacker has a way in to the network. From there, they can focus on privilege escalation to compromise other, more lucrative systems.
Solutions
What amazes me about these, especially when it comes to industrial controls and red light cameras, is how long they’ve been vulnerable. These things have been searchable on Shodan since at least 2013, and many of these are still connected, and still with no authentication necessary.
While many IoT devices, such as refrigerators or TVs, don’t need to be accessible from outside of the network that they’re on, other devices having remote access capabilities are understandable. Users with things like networked security cameras want to be able to view the footage remotely. Car wash and gas station owners want to be able to monitor certain statistics, such as soap or gas levels, without having to physically be on location. These things are understandable, and I’m not discouraging the practice. But what needs to be understood with these systems is that they have to be configured. Never leave any device that is accessible from the Internet with the default username and password. Many of these examples were accomplished by supplying such passwords as “admin” or “password.”
Also, home router and network configuration is important as you start to add IoT devices. As I said above, your refrigerator or TV don’t need to be publicly accessible outside of the home, but they do need to be able to get data to and from the Internet for patches and firmware updates. So it’s important to make sure that these devices don’t have unnecessary ports open, only the ports needed for the device to function, and firewall them so that they aren’t susceptible to malicious traffic.
Finally, make sure these systems are up to date on patches. Regularly patching your systems, especially IoT devices, will protect against any known exploits to those systems, helping keep your devices safe, which in turn will keep your home or business safe.
If you need further consultation for securing your devices, feel free to contact me to schedule one today!